Restrict the access to SOA Composite Service based on the User Role (Authorization to the SOA Composite Service) – Oracle SOA Suite 12c
Sometimes we may need to restrict the access to the SOA composite service based on the user role.
HTTP basic authentication and an authorization policy can be used to ensure that access is only granted to users who are members of a particular role.
This blog will explain the steps to enable authorization to our composite service.
Configure the Users and Group:
- Login to the Weblogic console ('http://<host>:<port>/console')
- In the left menu select 'Security Realms'
- Select the realm where you want to create the users and groups. The default is 'myrealm'
- At the top select the 'Users and Groups' tab
- Select User tab and Click 'New' and enter your user name and pwd. Here am creating the user albin and albin1, create as many users as you want
- Select ‘Groups’ tab and create a new group. Here I am creating ‘IntegrationGroup’
- Go back to the users and click on 'Albin'
- Select the 'Groups' tab and add ‘IntegrationGroup’. The user albin1 will not be part of this group.
Configure the Application Role:
- Login to EM console
- Click on Target Navigation - WebLogic Domain - Domain Name
- Click on Weblogic Domain - Select Security and Click on Application Roles
- Select Application Stripe as soa-infra
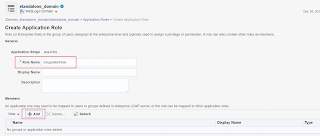
- Click on 'Create' to configure a new Application Role
- Enter the Role name as ‘IntegrationRole’
- Click on Add in the Member section
- Select "Check to enter principal name here instead of searching from above. This option can be used for advanced scenarios related to custom authenticators."
- Enter the Principal Name - IntegrationGroup and Click OK
Create the Application Policy:
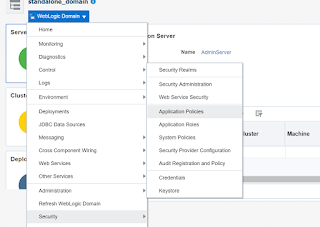
- Right Click on WebLogic Domain from Em console -- > Select Security and Click on Application Polices
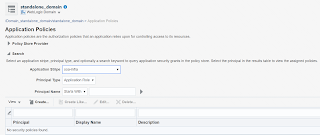
- Select the Application Stripe as soa-infra and Click on Create button
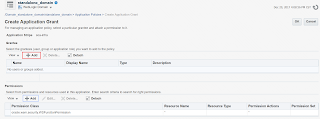
- Click on the Add button in the Permissions section to configure the Permission details.
- Click on Continue
- In the Customize section enter the Permission Class as oracle.wsm.security.WSFunctionPermission and enter '*' for both Resource Name and Permission Actions (In the actual implementation instead of “*” you have to specify the exact value) and Click Select.
- Click on the Add button in the Grantee section to add grantees for the Policy.
- Search for the Principal name starts with Integration
- Click on OK
Configure the Authentication/Authorizations policy to the Composite Service:
- Open the composite.xml
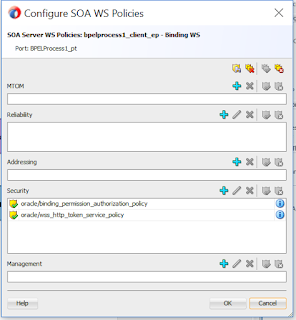
- Right click on the client service and click on Configure SOA WS Polices - For Request
- Add the security Policy oracle/wss_http_token_service_policy and oracle/binding_permission_authorization_policy for authentication/authorization in the security section.
Deploy the composite to the server. The same policy configuration can also be done through EM console after the deployment of the composite.
Testing From SOAP UI:
First try with the user ‘albin’; we will receive the success response message from the server.
Try with the user ‘albin1’; we will receive the Authorization error response message from server.










No comments:
Post a Comment